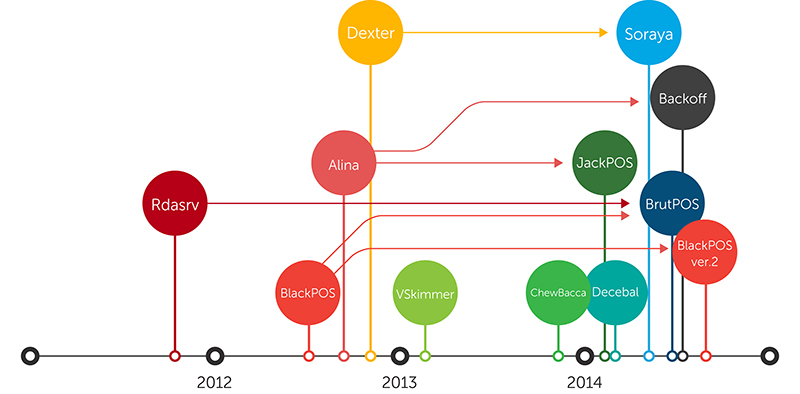
What Retailers Need to Learn from the Target Breach to Protect against Similar Attacks - Security Intelligence

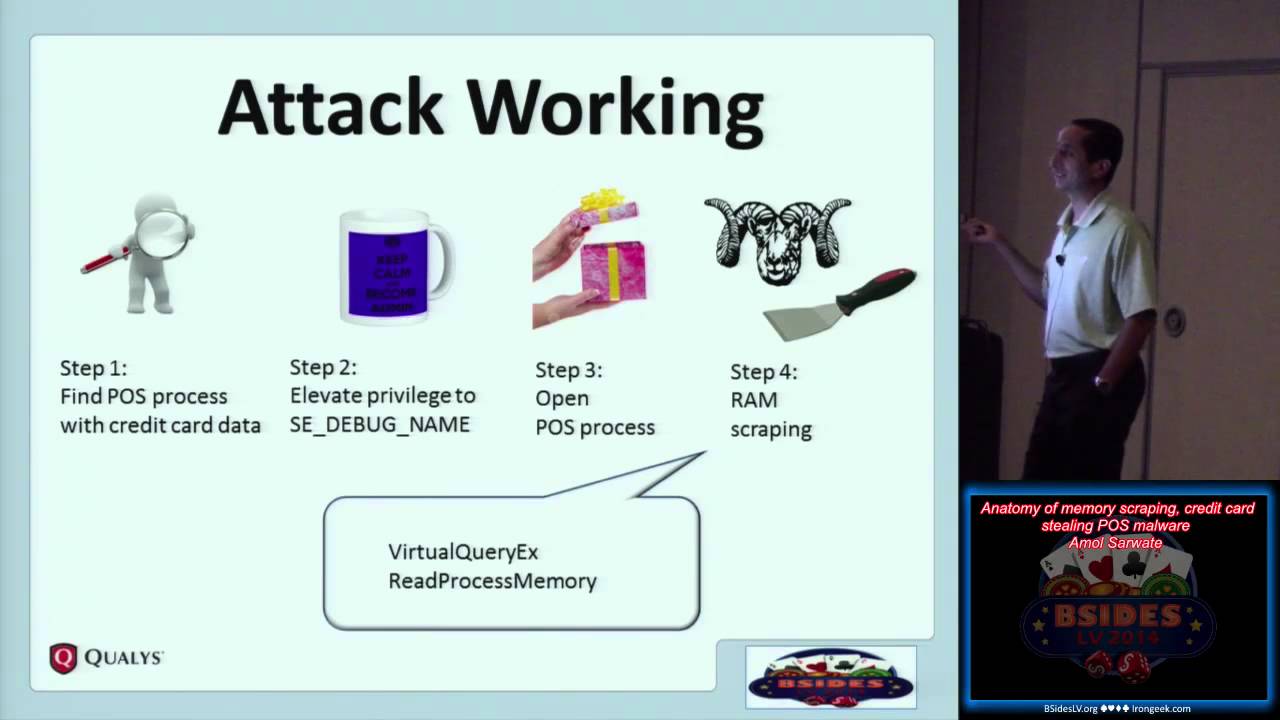
Defending Against PoS RAM Scrapers: Current Strategies and Next-Gen Technologies - Nouvelles de sécurité - Trend Micro FR

Ram-Pro 110 W Sticker and Adhesive Remover - Long Handle Floor Wall Scraper Tool Hot Blade Decal Remover Razor Blade Scraper Pinstripe Remover Hot Knife Blade for Removing Vinyl Decals : Amazon.ca:

An Identity Based Encryption Scheme Resilient to RAM Scraper Like Malware Attacks: Glassbox Secure IBE: Das, Dipanjan, Bose, Priyanka: 9789994980918: Amazon.com: Books